Critical Chain/Buffer Management: Sizing project and feeding buffers
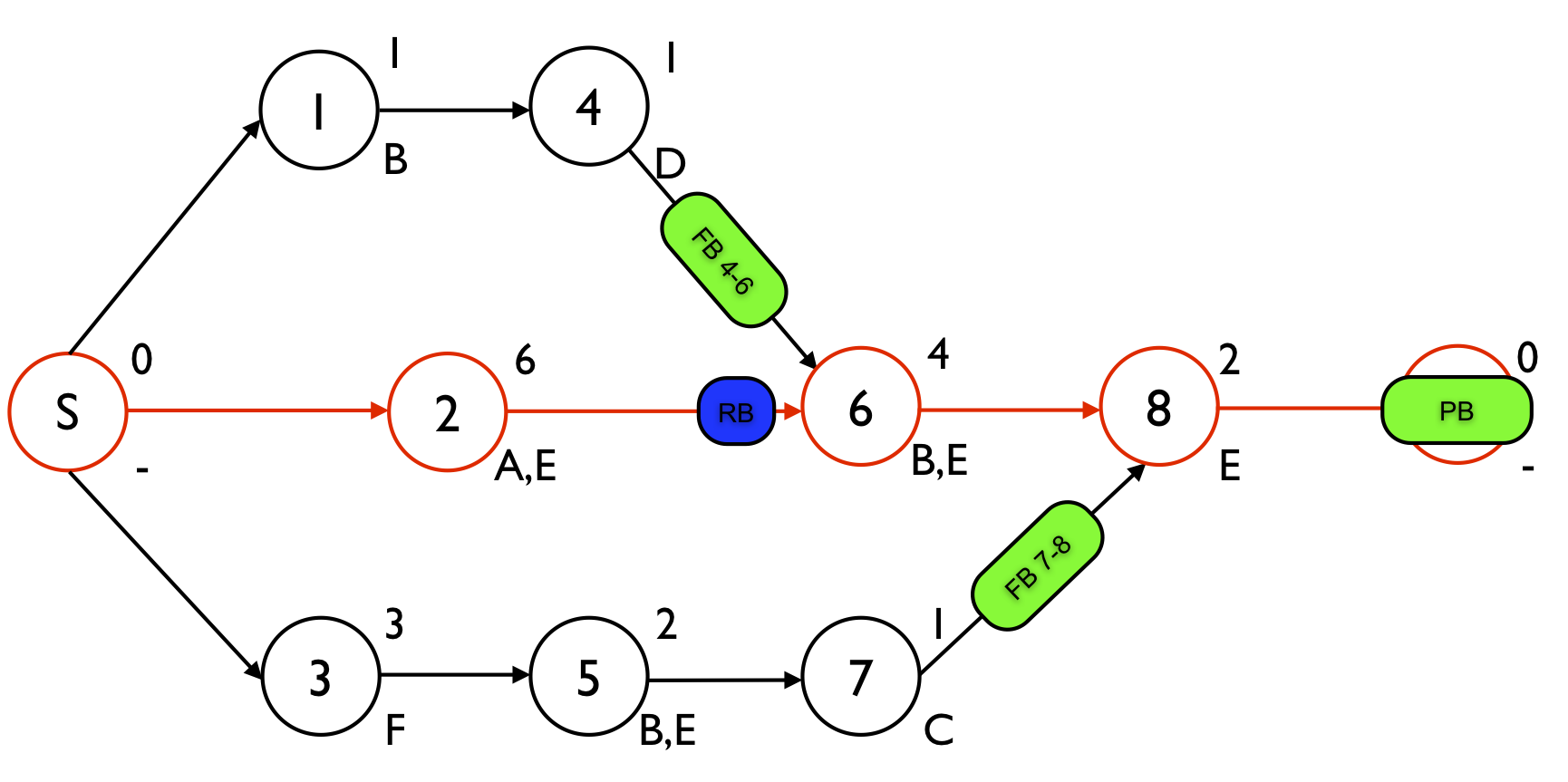
The Critical Chain/Buffer Management (CC/BM) approach uses project and feeding buffers to add safety time to the project baseline schedule and to guarantee the timely completion of the project with a high probability. Buffers are sized according to the properties of the path or chain feeding those buffers, such as the length of the path, its total variance, its average resource use or the number of activities it contains. In this article, a non-exhaustive overview of buffer sizing methods is given. Moreover, an example project is given in figure 1 which is based on other CC/BM articles and which will be used to illustrate the different buffer sizing methods in detail in other articles.
| Activity | Safe duration | Aggressive duration | Delta duration | Standard deviation |
| 1 | 2 | 1 | 1 | 0.5 |
| 2 | 9 | 6 | 3 | 1.5 |
| 3 | 5 | 3 | 2 | 1.0 |
| 4 | 2 | 1 | 1 | 0.5 |
| 5 | 3 | 2 | 1 | 0.5 |
| 6 | 6 | 4 | 2 | 1.0 |
| 7 | 2 | 1 | 1 | 0.5 |
| 8 | 3 | 2 | 1 | 0.5 |
- Critical chain 2 - 6 - 8: sqrt(1.52 + 12 + 0.52) = 1.87
- Feeding chain 1 - 4: sqrt(0.52 + 0.52) = 0.71
- Feeding chain 3 - 5 - 7: sqrt(12 + 0.52 + 0.52) = 1.22
| Buffer size method | Description | Reference |
| Cut and paste method | Buffer sizes are based on the duration of the chain feeding the buffer | “Sizing CC/BM buffers: The cut and paste method” |
| Root Squared Error Method | Buffer sizes are based on risk in the activity durations | “Sizing CC/BM buffers: The root squared error method” |
| Adaptive procedure with density (APD) | Buffer sizes are based on the structure of the partial network to which the chain belongs | “Sizing CC/BM buffers: The adaptive procedure with density” |
| Adaptive procedure with resource tightness (APRT) | Buffer sizes are based on the average resource use of the resources used by the activities on the longest path of the chain | “Sizing CC/BM buffers: The adaptive procedure with resource tightness” |
© OR-AS. PM Knowledge Center is made by OR-AS bvba | Contact us at info@or-as.be | Visit us at www.or-as.be | Follow us at @ORASTalks


